News

Was There Election Fraud In Michigan? Patrick B...
Discussions on election fraud related to the Michigan November 2020 Election, investigation and analysis of official election data in Michigan performed by the Election Integrity Force, and other election integrity...
Was There Election Fraud In Michigan? Patrick B...
Discussions on election fraud related to the Michigan November 2020 Election, investigation and analysis of official election data in Michigan performed by the Election Integrity Force, and other election integrity...

Bringing You The Evidence of a Stolen Election
The evidence presented herein should be enough proof for We the People to call for an immediate country-wide decertification of the November 3, 2020, election.
Bringing You The Evidence of a Stolen Election
The evidence presented herein should be enough proof for We the People to call for an immediate country-wide decertification of the November 3, 2020, election.

Michigan Election Evidence: Cyber Fraud
According to the graphical data above, early on November 4, 2020, there was a sudden injection of 384,733 ballots into the Michigan state voting tally across 4 Michigan counties (Wayne,...
Michigan Election Evidence: Cyber Fraud
According to the graphical data above, early on November 4, 2020, there was a sudden injection of 384,733 ballots into the Michigan state voting tally across 4 Michigan counties (Wayne,...
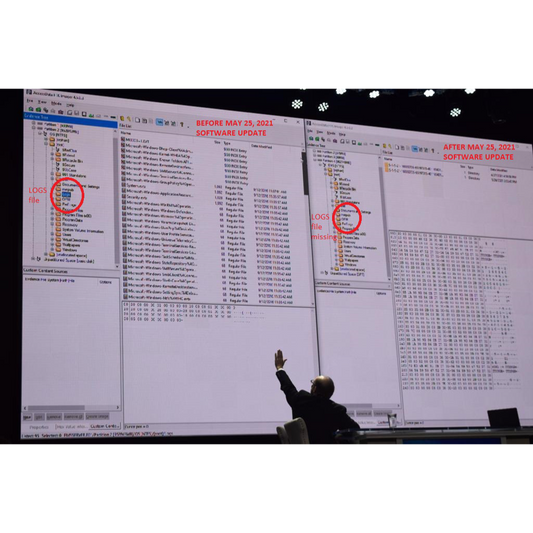
Irrefutable Forensic Evidence Dominion Deleted ...
Cyber Symposium Day 2 Recap 1 MESA COUNTY, COLORADO HEROICS Tina Peters, the Mesa County, Colorado clerk is a heroine and deserves a badge of honor. Instead she is being...
Irrefutable Forensic Evidence Dominion Deleted ...
Cyber Symposium Day 2 Recap 1 MESA COUNTY, COLORADO HEROICS Tina Peters, the Mesa County, Colorado clerk is a heroine and deserves a badge of honor. Instead she is being...
